

Overview
Audit Supabase RLS policies and detect exposed API keys (AWS, Stripe, OpenAI, GitHub, Google & 10+ more) in web applications.
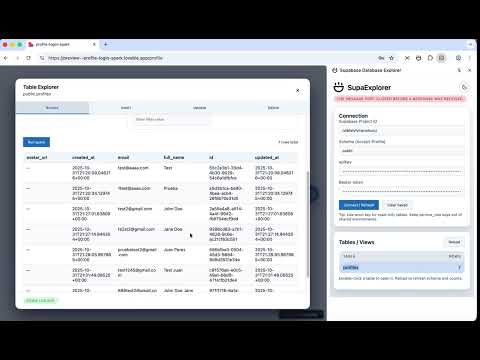
SupaExplorer: stress-test your Supabase security and detect API key leaks without leaving the browser Built for vibecoders, red-teamers, and security engineers hardening web applications. Primary focus on Supabase security auditing, with bonus API key leak detection across 30+ popular services. Why it matters Supabase Security Testing: - Surface hidden exposure fast. SupaExplorer auto-detects Supabase calls on any page, grabs the credentials in context, and shows you exactly which Project ID and schema are in play. - Catch hard-coded Supabase keys. With the DevTools panel open, SupaExplorer scans script/JSON responses for Supabase URLs and JWT keys—even when no request has been sent yet. - Audit RLS at a glance. The side panel enumerates every table/view, reports row-count permissions, and flags 401/permission-denied responses so you instantly see where policy gaps live. - Reproduce exploits safely. Double-click a table to launch the in-page explorer, then probe with read/write operations (select, insert, update, delete) against the same headers your app uses—no reconfiguring curl or Postman. - Export Supabase findings. Generate a printable security report that captures table exposure, row counts, and tailored remediation guidance. API Key Leak Detection: - Detect exposed credentials instantly. Automatically scan network responses for API keys from AWS, Stripe, OpenAI, and 15+ more services. - Comprehensive leak log. Track all detected keys in the DevTools panel's "Leaks" tab with matched values, pattern types, context snippets, and source URLs. - Zero configuration. Scanning runs automatically while the DevTools panel is open—no setup required. - Automatic deduplication. Identical leaks from the same source appear only once to reduce noise. Universal Benefits: - Reset on navigation. When keys disappear or you leave the app, SupaExplorer wipes its state so you're always testing live context, never stale creds. - Privacy first. All scanning and analysis happens locally in your browser—nothing leaves your machine. What's inside Supabase Testing: - Background sniffing via webRequest + fetch/XMLHttpRequest instrumentation to capture Supabase API keys and bearer tokens as they flow. - Chrome side panel UI for persisting project settings, toggling themes, and enumerating tables with live row-count status. - Modal explorer powered by PostgREST for quick CRUD checks and payload experimentation. - Security report composer that samples accessible tables, runs risk heuristics, and renders a ready-to-share PDF-friendly summary. - Static asset scanner in DevTools that flags embedded Supabase credentials pulled from captured bundles. - Floating SupaExplorer bubble that confirms detection and nudges you to open the side panel from the toolbar. API Key Leak Detection: - Pattern-matching engine with 15+ API key signatures for many services. - Real-time network interceptor that scans JavaScript bundles, API responses, HTML documents, and JSON payloads. - DevTools leak log showing matched values, pattern types, surrounding context, and source URLs. - Deduplication cache to prevent duplicate leak entries from the same source. Shared Infrastructure: - DevTools panel as a unified hub for both Supabase detections and API key leaks. - Local-only processing—no data transmission to external servers. - Automatic state cleanup when navigating away from monitored sites. Ideal use cases - Security engineers validating Supabase RLS policies and scanning for exposed API credentials before production launch. - Red teams and penetration testers looking for credential leaks and database misconfigurations during engagements. - Developers auditing their own apps to catch accidentally committed API keys in bundled JavaScript. - Bug bounty hunters searching for Supabase RLS bypasses and API key exposures in web applications. - DevOps/SRE teams investigating incident reports involving leaked credentials or database access issues. - Code reviewers checking staging environments for hard-coded secrets before code reaches production. - Security researchers analyzing third-party SaaS platforms for credential exposure vulnerabilities. Safety notes - Privacy first: All credentials, leak reports, and analysis stay local in `chrome.storage.local`; nothing leaves your machine. - Respect RLS: SupaExplorer highlights Supabase permission errors rather than trying to bypass them. - Ethical use only: Use API key detection for authorized security testing, code reviews, and incident response—never for malicious purposes. - False positives possible: The leak scanner uses pattern matching; always verify findings before taking action. - For sanctioned penetration testing, pair with anonymized datasets, scoped service-role keys, and proper authorization.
0 out of 5No ratings
Details
- Version1.0.0
- UpdatedNovember 25, 2025
- Size87.65KiB
- LanguagesEnglish
- DeveloperWebsite
Email
apps@aberastegue.com.ar - Non-traderThis developer has not identified itself as a trader. For consumers in the European Union, please note that consumer rights do not apply to contracts between you and this developer.
Privacy
This developer declares that your data is
- Not being sold to third parties, outside of the approved use cases
- Not being used or transferred for purposes that are unrelated to the item's core functionality
- Not being used or transferred to determine creditworthiness or for lending purposes
Support
For help with questions, suggestions, or problems, visit the developer's support site