

Overview
OWASP Penetration Testing Kit
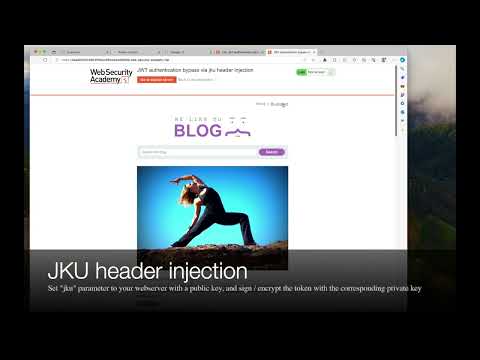
The Penetration Testing Kit (PTK) browser extension is your all-in-one solution for streamlining your daily tasks in the realm of application security. Whether you're a penetration tester, a member of a Red Team, or an application security practitioner, this extension is designed to enhance your efficiency and provide valuable insights. Key Features: In-Browser Runtime Scanning: PTK offers Dynamic Application Security Testing (DAST) and Software Composition Analysis (SCA) scanning right within your browser. Detect SQL Injections, Command Line Injections, Stored and Reflected Cross-Site Scripting (XSS) vulnerabilities, and more. It even identifies complex threats like SQL Authentication Bypass, XPath injections, and JWT attacks. JWT Inspector: We've added a crucial new feature – JWT Inspector. It empowers you to analyze JSON Web Tokens (JWT), build new tokens, and generate public and private keys for JWT signing. PTK makes easy a lot of JWT attacks including null signature, none algorithm, brute force HMAC secret, key/algorithm confusion, JWK injection, JKU injection, and kid parameter injection. Insightful Information: Get a one-click access to insightful information about the target application, including its technology stack, Web Application Firewalls (WAFs), security headers, crawled links, and authentication flow. Proxy with Traffic Log: PTK includes a proxy with a detailed traffic log. This log allows you to repeat any request in the R-Builder or send it to the R-Attacker. You can automate the execution of Cross-Site Scripting (XSS), SQL injection, or OS Command injections. R-Builder for Request Tampering and Request Smuggling: The extension includes R-Builder, a powerful tool that allows you to craft and manipulate HTTP requests with precision. Use R-Builder to modify and tamper with requests, enabling you to test the robustness of the application's security. R-Builder empowers you to execute complex maneuvers, including HTTP request smuggling attacks, for a comprehensive assessment of application vulnerabilities. Now with cURL support - copy or paste your cURL request and execute in a second. Cookie Management: The extension includes a cookie editor, allowing you to manage cookies efficiently. Add, edit, remove, block, protect, export, and import cookies with ease. Decoder/Encoder Utility: The integrated utility helps you manage encoding and decoding from and to various formats, including UTF-8, Base64, MD5, and more. Swagger.IO Integration: We've integrated Swagger.IO to enhance your understanding of API documentation. Easily create requests to interact with API endpoints. Selenium Integration: With Selenium integration, PTK aids in identifying security risks at the early stages of the development cycle, ensuring robust security from the outset. Enhance your application security practices with PTK, the browser extension that makes your browser smarter. Whether you need to uncover vulnerabilities, analyze JWT tokens, or optimize your security workflow, PTK has got you covered. Try it today and take your application security to the next level.
4.8 out of 543 ratings
Google doesn't verify reviews. Learn more about results and reviews.
Dan CristinoAug 30, 2024
Works on Chrome and other Chrome-based browsers. Sadly, won't work on Arc browser :(
Przemysław SamselApr 13, 2024
Helpful stuff thanks!
gideon adavizeJan 26, 2024
Wonderful extension
Details
- Version8.9.3
- UpdatedMay 6, 2024
- Size7.14MiB
- LanguagesEnglish (UK)
- DeveloperWebsite
Email
denis.podgurskiy@gmail.com - Non-traderThis developer has not identified itself as a trader. For consumers in the European Union, please note that consumer rights do not apply to contracts between you and this developer.
Privacy
OWASP Penetration Testing Kit has disclosed the following information regarding the collection and usage of your data. More detailed information can be found in the developer's privacy policy.
OWASP Penetration Testing Kit handles the following:
This developer declares that your data is
- Not being sold to third parties, outside of the approved use cases
- Not being used or transferred for purposes that are unrelated to the item's core functionality
- Not being used or transferred to determine creditworthiness or for lending purposes
Support
For help with questions, suggestions, or problems, please open this page on your desktop browser